There's no point denying the harsh reality: no industry in the digital era can mark itself 100% safe from cyberattacks. Moreover, the evolution of cybersecurity threats over the last few decades has bothered business owners and CEOs. Attack modules have increasingly gained sophistication, from ransomware attacks to phishing and information theft to malware attacks. So, what's your counter-strategy to combat potential security threats for your organization?
As we look deeper into the evolution of cybersecurity threats, the menacing reality surfaces before us.
- In 2022, businesses and government organizations recorded 2,200 cyberattacks on average daily.
- The first half of 2022 witnessed more than 2.8 billion malware attacks.
- Every 39 seconds, someone records a data breach in the US.
- At any given time, as many as 4.1 million websites have malware.
- The gradual evolution of cybersecurity threats is currently causing stress for 60% of CISOs.
No wonder the evolution of cybersecurity threats deserves the attention of CEOs and data security officials.
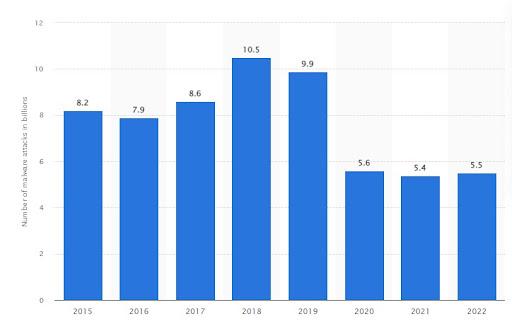
This graph shows the number of global malware attacks between 2015 and 2022. In 2022, this figure stood at 5.5 billion, rising marginally over the previous year.
Evolution Of Cybersecurity Threats: How Does Global Cybercrime Stand?
As businesses step into the digital business paradigm, they encounter a new host of attack modules. With the development of technology, attack modules are also gaining sophistication. No wonder why global cyber gangs are now much more resourceful compared to what they were a decade ago. The risk profile for businesses operating in the digital landscape looks much more intense.
Let's closely examine the evolution of cybersecurity threats over the last decade across the globe.
Cyber-Crime-as-a-Service
Information is the most powerful currency in the digitized business environment. This explains why businesses need to take a stand against information theft. Cyber gangs offer lucrative services to competitor companies, providing cybercrime as a service. Skilled cybercriminals deploy ransomware and malware to break into information systems and steal data.
Besides, ransomware's menace remains fresh in most CEOs' minds. So naturally, the evolution of cybersecurity threats has prompted business leaders to take adequate countermeasures and train their employees to combat the challenges.
Given that hacking and cybercrime are now available as a service, the threat paradigm seems even more ominous.
Remote Procedure Call Exploits
Talking about the rapid evolution of cybersecurity threats, one must recognize remote procedures called exploits. A Microsoft RPCE, often called a subroutine call, is a client-server protocol. MSRPC aims to allow a program to use another program to call a service on a different information system without knowing the respective network.
With the evolution of cybersecurity threats, attackers are abusing the MSRPC calls to launch cyberattacks like enumeration, lateral movement, credential dumping, and privilege escalation. Since most businesses fail to remain abreast with adequate countermeasures for these attacks, cybercriminals exploit the vulnerabilities.
LOTL/Fileless Malware
The evolution of cybersecurity threats is evident from the inception of file-less malware and LOTL attacks. Unfortunately, this sophistication often beats modern countermeasures, making identifying the attack difficult. Under this attack module, cyber criminals use a file-less technique or deploy a LOTL (living off the land) mechanism to intrude into the system. Besides, these attacks use the system's commonly used tools and utilities to inflict more damage.
Cyberattacks do not write file-less malware to disk, and the malicious code operates in volatile memory. However, due to the evolution of cybersecurity threats, cybercriminals have come up with this mechanism that manages to evade endpoint protection since the system doesn't have any files to scan.
Since the attacker uses the system tools, the security breach often remains undetected. However, the system administrators need clarification, as they use the same devices, such as Windows Management Interface (WMI), PsExec, and PowerShell, for daily operations.
Compromising Supply Chains
Cybercriminals are deploying a relatively new attack module called supply chain compromise. During the attack, the adversary compromises a service provider, hardware, software, or manufacturer. With the evolution of cybersecurity threats, dishonest players in the industry have realized that targeting resource-oriented businesses can give them an advantage in the respective domain.
Some recent supply chain compromises include the attacks on Log4j, Kaseya, and SolarWinds. In the Kaseya and SolarWinds supply chain attacks, the criminals compromised the servers of the software vendors to inflict malware on the victims. The Kaseya attack, for instance, involved more than 1,000 organizations bearing the burn of ransomware infection.
This evolution of cybersecurity threats is not here to stop. Attack modules will likely get even more potent in the coming years. This calls for a comprehensive defense mechanism for organizations operating on digital platforms.
Phishing
Although phishing remains one of the most primitive attack modules, the evolution of cybersecurity threats has witnessed the inception of new phishing methods. For instance, spear and whale phishing are much more sophisticated than traditional email phishing.
As a social engineering technique to gain unauthorized access to data, phishing techniques continue to haunt business owners. The attacker, under this module, tricks a potential victim into carrying out an unsolicited action. The victim enters sensitive personal details like email IDs or account passwords into a fake portal replicating the original.
Often, phishing attacks come with a sense of urgency. Also, the attackers turn out to be imposters, and they might pose as government or fund collection officials. With the gradual evolution of cybersecurity threats, other attack modules have become popular. However, in the first quarter of 2022, phishing accounted for the most used attack module for the financial industry (23.6%).
Ransomware
Do you know that 71% of businesses became ransomware victims sometime in 2022? Besides, IBM states that, on average, organizations took as long as 49 days to identify a ransomware attack! Close to three-quarters of IT professionals shelled out the ransom so that they could recover from the attack.
The problem with ransomware is that it uses a vulnerable system to encrypt its data. As a result, the victim fails to access valuable information stored on their system unless they fork out the ransom or fee to the attacker. The memories of the ill-famous Wannacry ransomware in 2017 might still be fresh in your mind.
Apart from stealing your data, the attackers take resort to extortion. With the evolution of cybersecurity threats, cybercriminals are keen to maximize their gains!
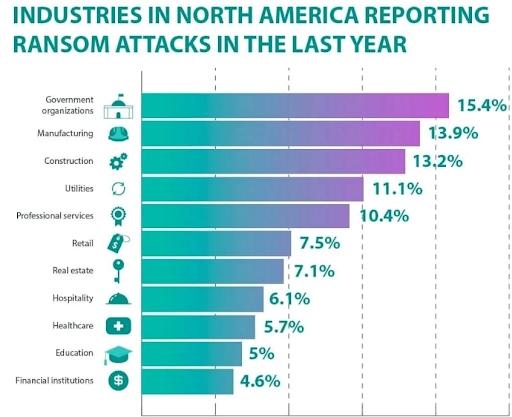
This chart shows that government organizations, followed by several prominent retail industry sectors, were the prime targets of ransomware attacks in 2022.
Combatting Cybersecurity Threats: How To Stay Ahead Of Attacks?
With cyberattacks on the rise, it's time to strengthen your line of defense against the culprits. So besides checking the vulnerabilities in your system, it pays to train your employees to develop a new level of cyber resilience.
While firewalls and antivirus are already in place, only some prove to be 100% effective against social engineering attacks. Therefore, the defensive stance against cybercriminals amidst the evolution of cybersecurity threats must stem from conscious internet use.
We have highlighted some effective countermeasures to combat the menacing threat of cyberattacks.
Risk Analysis And Management
Assessing potential risks that your business might face in terms of cybersecurity is a crucial part of risk analysis. Accordingly, you can strengthen your countermeasures and reduce your risk profile.
Forward-thinking businesses have already been collaborating with cybersecurity professionals and service providers to leverage their defensive stance. Risk analysis is followed by risk management, which involves a wide range of quantitative and qualitative techniques. Cybersecurity experts even deploy mathematical and statistical analysis to evaluate the chances of potential consequences.
As a part of risk management, businesses can design effective methods. Here are some of the steps involved in the risk mitigation process:
- Risk evaluation
- Risk acceptance
- Risk avoidance
- Risk mitigation
The best way to counter the gradual evolution of cybersecurity threats is to avoid the risk in the first place. Therefore, businesses should have a proper plan to identify potential threats and root them out.
Seeking Managed Cybersecurity Services
The consistent evolution of cybersecurity threats has prompted global organizations to outsource their cybersecurity services. As a result, businesses in the digital business environment habitually seek managed cybersecurity services from IT experts. Established professionals secure their network and ensure zero data breaches.
Here are some of the security services that you can outsource to professionals.
- Assessments and security audits: This involves the scrutiny of the security status of your organization. Accordingly, the experts can detect potential vulnerabilities in your network.
- Solution implementations: On evaluating your organization's risk profile amidst the evolution of cybersecurity threats, IT experts recommend strategic solutions exclusive to your business.
- IT security staffing: Managed cybersecurity services also include IT security staffing. This way, you can benefit from assistance, insight, and advice from professionals in the IT industry to maintain cyber-solid resilience.
Formulating Policies For Cybersecurity
One of the most effective means to combat the evolution of cybersecurity threats is to come up with a comprehensive policy to strengthen your organization's cybersecurity. This policy should define the approach of every staff on your platform to manage cyber threats and nullify the same. Here are some of the common cybersecurity policies that businesses must deploy.
- Formulate an information security policy that defines how your employees are supposed to manage confidential information. This includes access restrictions, data encryption, and effective processes for reporting incidents.
- Have a foolproof acceptable use policy to establish standards governing how your employees must conduct themselves amidst the evolution of cybersecurity threats. This policy must define how employees must use your organization's resources, such as PCs, software, and networks.
- Articulate a strong password policy that outlines the principles for maintaining strong passwords.
- Create an incident response policy outlining the necessary steps during a data security breach. It should also outline how to report the incident and steps to mitigate the risk.
- Organizations need to have a remote access policy that prescribes relevant guidelines to their staff in using VPNs and other tools to access the organization's resources remotely.
- Your compliance policy should define the organization's adherence to the established cybersecurity policies, standards, and norms.
- Make sure to frame your third-party vendor management policy to define how you will deal with the rights associated with external service providers and suppliers. This includes contractual agreements and security evaluations of third parties.
- A disaster recovery and data backup policy would further strengthen your defensive stance amidst the evolution of cybersecurity threats. It defines your tactics for disaster recovery and data backup. These policies also govern disaster recovery protocols, off-site storage, and making routine backups.
- Lastly, make sure to formulate a policy for employee training and awareness. From time to time, educate your staff about the latest cybersecurity threats to strengthen your stance against adversaries holistically.
Tips To Strengthen Your Cybersecurity Stance
The evolution of cybersecurity threats has prompted CEOs and business owners to integrate the latest firewalls, antivirus, and other protective mechanisms to strengthen their defense against cybercriminals. Here are some additional guidelines that might prove handy for your organization.
- Device and network security: As you brace to encounter sophisticated online threats, strengthen your network and device security. Forward-thinking organizations are already integrating intrusion detection systems, firewalls, and antivirus犀利士
tools from top and reliable brands like McAfee, Kaspersky, Norton, etc. - Filtering emails: Make sure to filter every email, both incoming and outgoing, so that you can weed out the possibilities of phishing attacks in your network.
- Access control: Being the organizational head, deploy stringent regulations for access control. This ensures that only authorized staff would be able to access essential systems. Also, deploy strong policies for managing passwords and have MFA in place. Update your passwords regularly and keep an eye on the log user accesses.
- Monitoring network traffic: Monitoring your network traffic would enable you to identify security issues instantly and respond to them in real-time. Also, keep all your software updated and fix the bugs.
- Data encryption: Encrypt data on your network to secure sensitive information during transit or storage. Secure all the information stored in portable electronic devices, laptops, and computers.
Wrapping Up
Well, the playbook for online criminals keeps expanding with the inception of new technologies. We have explained the evolution of cybersecurity threats in the digitized world besides recommending effective means to stay secure from attackers. With these measures, you can keep your data resources intact and secure.
Securing your business from cybercriminals would add to its integrity and stability. However, as the evolution of cybersecurity threats continues to threaten your data integrity, ensure a powerful cybersecurity program is in place. This will protect your organization against unauthorized data access, theft, and ransomware attacks.














Leave a Reply