If you were to ask us, the third world war would be a series of cyberattacks.
Cyber attacks, regardless of their severity, require to be dealt with proactively.
Cyber analysts use cyber threat intelligence like tactical intelligence to detect and mitigate cyber threats before they cripple us. In this blog, we will go through an overview of cyber threat intelligence.
Here's your complete guide to threat intelligence.
Table of Contents
What Is Cyber Threat Intelligence?

Cyber threat intelligence is information an organization uses to understand whether their organization has any cyber threats or will have any threats in the future.
Cyber threats are dangerous, and they can bring any organization to its knees.
However, threat intelligence can help various organizations gather helpful information about the threats and develop an effective defense mechanism.
Cyber threat intelligence is extracted from multiple sources like:
- open-source intelligence
- social media intelligence
- human intelligence
- technical intelligence
- intelligence from the deep and dark web
How Does Threat Intelligence Work?
Threat intelligence requires the collection of information on the threats. Then there is a need to consolidate all cyber threat intelligence sources - both external and internal - into a single common location to automatically achieve a single source of truth. Therefore, aggregation becomes important while using cyber threat intelligence to save time and labor.
Then next, there is the contextualization of the data to speed up the process as the context provides a better understanding of the threat and its nature. Then the data collected for threat intelligence is prioritized to ensure the right threats are dealt with first.
It is essential to regularly assess the information to ensure that the defense mechanism does not fail against any cyber threats. Therefore, cyber threat intelligence must be updated and improved periodically to make the intelligence work better and make better decisions about potential threats.
Why Is Threat Intelligence Important?

As mentioned above, cyber threats are dangerous for any organization as they can cause the entire organization to shut down. This danger is the genuine concern of every organization. Companies use cyber threat intelligence platforms to tackle cyber threats, which help them provide early warnings of any threat their company will face.
Threat intelligence programs collect large amounts of raw data from various available sources on emerging or existing threats. The data collected is then examined and prioritized to provide threat intelligence responses and the management reports which carry the information for automated security control solutions. The main objective behind all this is to keep the organizations posted about the threats and the possible solutions.
Types Of Threat Intelligence
There are mainly three types of cyber threats intelligence categorized as strategic, tactical, and operational.
- Strategic Intelligence- Strategic threat intelligence is basically for the executive-level security analysts to work for the high-level organizational strategic approaches based on the details found in the management reports. Moreover, it is for a less technical audience. It provides a basic overview based on a detailed analysis of trends and emerging threats to create a landscape and provide information on the vulnerabilities and threats the organization can face.
- Tactical Intelligence- Tactical intelligence works on the building of defense strategies to mitigate cyber threats. It consists of precise information on the tactics, techniques, and procedures(TTP) of an organization's threats. It provides the reports to the organizations which include the Indicators of Compromise (IOC) like IP addresses or URLs or System Logs, vulnerabilities and loopholes in the security management of the company that attackers could take great advantage of, as well as provides the information on how to identify such attacks.
- Operational Intelligence - Each cyber threat has its nature, motive, timing, and way it is carried out. The operational threat intelligence provides knowledge of these components of the threat to the organizations.
Threat Intelligence Program Steps
Step 1: Requirements and plans for cyber intelligence
Cyber-Intelligence begins with understanding cyber-intelligence requirements and who and in what format will consume that intelligence. Identifying the organization's significant risks and evaluating the existing cybersecurity landscape make the requirements more clear.
Step 2: Plan an Intelligence Threat Program
Planning requires budgeting that will determine the overall cyber security operations of an organization. It requires people, process, and technology to create a framework to keep the stakeholders informed. Planning is incomplete without the support of management as they create the policies and plans of projects which are further carried out by the teams. Therefore, having the c-suite members on board is imperative.
Step 3: Create an Intelligence Threat Team
Security analysts need to gather and analyze threat data for diverse stakeholders to provide actionable insights; this is a high-stakes task. Therefore, in the threat intelligence team, it is vital to have certified analysts. One way to create a great threat intelligence team is to find cyber analysts with certification or with proven experiences. Training should also be an integral part of creating an intelligence threat team.
Step 4: Collection of Data
Data is gathered using internal and external sources such as network logs, previous event records, open and dark web, and social media. Therefore, intelligence analysts need to be clear on the kind of data they want, the tools and techniques they need to gather and store it.
Step 5: Processing of data
After collecting data, it becomes important to normalize it in a format and structure it well for further analysis. Data processing consists of decrypting, sorting, translating, sampling, and sorting the data collected.
Step 6: Analysis of threats
Threat analysis helps identify the trends and patterns of the threat with the help of data analysis tools and techniques when running across the collected data. This analysis then helps determine the security system components that need more protection to know about the kind of threat they are facing or might face.
Step 7: Dissemination of reports
Cyber threat intelligence works efficiently only when it is timely, provides context, and is easily understandable by the stakeholders who decide cybersecurity. Therefore, it is necessary to share the intelligence reports with appropriate stakeholders to take mandatory actions. The report should be shared promptly to act proactively against any future threat. In addition, these reports should be unambiguous.
Step 8: Feedback
When the stakeholder/security team receives and utilizes the cyber intelligence, they should give their feedback to assist the intelligence team for the next cycle of threat intelligence.
Feedback enables cyber intelligence analysts to enhance their threat intelligence program in the coming future by understanding the data to be collected and how it may be enhanced and processed to provide effective intelligence and communicate it to relevant stakeholders effectively.
Threat Intelligence Use Cases
The solution you select for threat intelligence depends on your company's requirements. When looking for a solution, it is vital to take a 'use-case' approach to see what threats solutions you need. Here are the five threat intelligence use cases:
1. Increase legacy security technology
Integrating threat intelligence into current security programs and solutions enhances reaction speed by increasing the knowledge about the threats. In addition, this enhances the capacity of your security team to spot risks and increases the timespan of legacy solutions to assist companies in optimizing security investment returns.
Look at the tools you presently use to discover where improvements should be made before selecting the threat intelligence solution. Threat intelligence solutions are built for the easy integration of existing systems. Thus choose tools that complement your particular safety needs.
2. Prioritization of threats
While using threat intelligence, the organizations can collect a large amount of data to determine the severity of the threat but this piling up data is not always useful. In addition, it can lead to losing focus from the actual threat.
Therefore, it is mandatory to prioritize the threat so that the data can be bifurcated systematically; this enables the analysts to establish a vulnerability ranking system of threats. Thus, the security teams can allocate time more efficiently while managing new emerging threats.
3. Monitoring the Open, Deep, and the Dark web
The data should be collected from open and closed sources on the internet for a suitable threat intelligence solution.
As we all know, open sources are sources of information publicly available to all.
The deep web refers to the secure connections or paywalls locked on the internet and out of the reach of search engine crawlers. This data comprises scientific, academic, or governmental reports and personal data such as bank or medical records.
The dark web is mostly a marketplace for illegal goods and activities, and it can only be accessed through web browsers like Tor that offer exceptional anonymity.
In the deep and dark web, the security system is managed so that both parties try to protect themselves, which results in exchanging and discussing the potential threats and vulnerabilities from which they both need safety. Therefore, the more the data collected from these sources, the more the intelligence can be fed to the threat intelligence data, preventing future cyber threats.
4. Safeguarding the brand image
The value of a brand is important, and to maintain the brand value, companies need to keep their organizational data and customer data safe from cyber-attacks.
Cybercriminal constantly tries to exploit critical data of the organizations for fraudulent purposes.
Malicious or fake social media profiles that have been accepted by your staff or even mimic your staff's profiles, malicious links that have been posted to your social media profiles, intellectual property loss, theft, and misuse, are some examples of cyber attacks that can tarnish your brand image.
But the threat intelligence solutions can stop the exploitation of data as threat intelligence provides a sneak peek into the techniques of the cybercriminals that are used to steal data. In addition, this intelligence can provide the security teams with real-time notification of any new strategy that any cybercriminal creates; this helps the brand keep its adversaries away.
5. Threat Indicator Investigation and Response
It is not possible to stop every potential cyber attack on the organization. Therefore, the major value of most threat intelligence solutions is the ability to improve your time of response to it and the accuracy of detecting a threat in the first place.
Focusing on prevention is significant, but that can only be achieved when the organization can detect and respond to the threats. Therefore, investigation and response are the basic components to prevent cyber threats. Therefore, threat intelligence solutions can be very helpful in this regard, enhancing the security layer of your organization and allowing on-demand access to submit files or objects. In addition, this helps in determining threat indicators like suspicious domain names, IP addresses, etc.
Handpicked Threat Intelligence Tools
Here are 8 threat intelligence tools that most cyber intelligence analysts recommend to safeguard your business against threat intelligence.
1. IntSights External Threat Protection (ETP) Suite
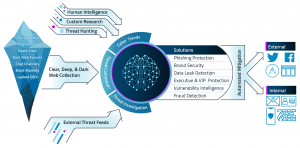
IntSights ETP assists businesses in fighting external threats by turning external threat data on their digital assets into useful operative security information.
The Threat Command provides tailor-made warnings and corrections for external threats aimed at your business and industry, which are collecting information on the clear, deep, and black web.
The platform gathers all your threats and enhances Indicators Of Compromise (IOC) for more detailed research. IntSights threat intelligence platform (TIP). IntSights Risk Risk Analyzer revolutionizes the patch process by evaluating, enriching, and rating Common Vulnerabilities and Exposures CVEs depending on risk severity.
It allows security teams to expand their visibility, recognize the dangers and automate responses using many threat indicators. In addition, the connection into your current safety pad allows for automatic coordination and reaction of threats.
Features:
- Risk Analyzer Vulnerability: Prioritizes critical vulnerability patches.
- Threat to third parties: Provides your stakeholders with quick deep web intelligence.
- Automated mitigation: risk mitigation and recommended actions.
2. DeCYFIR
The threat discovery platform for CYFIRMA, DeCYFIR, this tool uses deep technology and AI engines on the dark/deep website, closed communities, and forums for hackers to unearth, analyze, correlate and get the deepest insights from bright data.
Its modern threat response and cyber threat intelligence platform combine hackers, motives, campaigns, and techniques in a way that provides complete contextual information to assign cyber threats. Tactical, managerial, and strategic information are among the insights provided by the platform that advise safety teams and executives throughout the business.
Features:
- DeCYFIR: The only product in cyber-intelligence that customers can see the world from the viewpoint of hackers and comprehend how cyber threats, motives, methods, and campaigns interrelate. It identifies concealed signals with indicators of an imminent attack.
- Brand risk monitoring: promotes threat monitoring to defend your brand against dangers.
- Check for, and correlations of threats: DeCYFIR employs an external method in the correct location to find risks.
3. ThreatFusion
ThreatFusion offers a large-scale threat research module to assist Threat Intelligence teams in a deeper context, threat search, and analysis in real-time.
Data is gathered, from paste pages to underground dark web forums by enormous data sources throughout the surface, deep and dark web.
ThreatFusion provides a Big Data-driven threat research service. It allows safety personnel to search for risks and find a detailed context in real-time. ThreatFusion's suite gathers data from deep and dark websites and combines information from numerous sources to address threats to your sector.
Features:
- Dark web insights: It lets you get insight into the dark web to evaluate current and future dangers.
- Accelerated research: ThreatFusion helps you obtain quick and significant findings from the depths of the internet.
- Feeds ready for API: Intelligence about threats is analyzed to give exact outcomes.
4. Blueliv
Blueliv safeguards your networks from hackers and attacking viruses and provides a modern threat response. In addition, it leverages data APIs to create full customization and easily integrated plug-ins in your system.
Adding a new source in Blueliv's administration panel is as straightforward as adding a new Java or Python plug-in. It covers up the information and sends it to the customer as information arrives on the Blueliv platform. The Blueliv platform then enhances, standardizes, enriches, and correlates information and combines it with high-database storage for analysis.
Features:
- Versatile monitoring: It monitors botnets, credit cards, malware, deep internet, search engines, social media, hacktivism, phishing, mobile networking and applications, brand abuse, social surveillance, and leaks of information depending on the modules you install.
- Contextualized landscape threats: You receive personalized modern threat responses with threat evaluations by specialists.
5. Wildfire

The WildFire Analysis Environment discovers unknown malware and creates signatures that may be used to identify and disable the firewall in Palo Alto networks.
The sample for WildFire analysis can automatically be forwarded from a Palo Alto Network Firewall to an unknown sample (a file or e-mail link).
When it finds an unknown sample, based on the displays' features, behaviors, and activities, it concludes whether that sample is benign, grey, physical, or malevolent when examined and performed in the WildFire sandbox.
Wildfire automatically delivers cloud-based analysis for malware identification and prevention. In addition, it helps your business stop malware once continual monitoring and warnings are available in the system.
Features:
- Next-gen firewalls: Your firm remains on prevention-centric architecture with next-generation firewalls.
- Safety of DNS: It helps to interrupt assaults using DNS for data robbing.
- Safety subscription: It offers a variety of subscription services to enhance your safety.
6. ThreatQ
Your existing security infrastructure and personnel need to work smarter and not harder to recognize and stop attacks effectively and efficiently.
ThreatQ can act as an open and comprehensible threat intelligence platform that speeds security operations by streamlining and managing threats.
With an integrated, self-tuning library, adaptive workbench, and open interchange, dangers can be easily grasped, detected, and reacted to more rapidly.
It focuses on current and future threats to protect your business activities, helping you to prioritize risks and threats and work together with teams. Moreover, it addresses all conceivable flaws in the system with its vulnerability management.
Features:
- Threat Library: A central repository that enables security teams to discover prospective hazards with threatened elements.
- Ease of use: ThreatQ provides a comprehensive platform to adjust your work procedures and simplify them.
- Open exchange: You can connect your existing solutions into one platform with over 200 feed and product integrations.
7. ThreatConnect

ThreatConnect is a cybersecurity platform that provides decision and operational assistance.
It is the only system that integrates cyber risk quantification, orchestration and automation, analytics, and templated processes for all stakeholders, including security and business leaders, risk, vulnerability, operations, and response teams.
ThreatConnect assists you in making the best security decisions possible. For all stakeholders, it integrates cyber risk quantification, analytics, and automation natively. Financial services, government, healthcare, retail, and technology industries - all kinds of industries benefit from ThreatConnect's offering.
Features:
- Respondent: It records and analyses all data relating to the case that aids in detecting the problem and the accuracy of the incident.
- Brand monitoring: You may monitor numerous sources with ThreatConnect and track your brand performance under one roof.
- Phishing analysis: Each piece of information is manually examined to determine whether phishing in the business environment is not conceivable. ThreatConnect automatically checks phishing trials.
8. Kaspersky
Kaspersky's services offer you the intelligence that you need to minimize these risks from our world-leading scientific and analytic team.
Kaspersky has been the trusted partner of top international law enforcement agencies and government agencies like INTERPOL and leading CERTs with expertise and experience in each element of cyber-security.
Now in your organization, you can harness that intelligence. Kaspersky Lab gives you the latest statistics from various countries to provide you a thorough overview of the cyber threats your company is facing. In addition, it employs intelligence reporting to provide insights and techniques to improve safety checks.
Features:
- Reporting of financial risks: focuses on threats to financial institutions.
- Digital footprint information: identifies weak areas and identifies potential proof of assaults.
- Cloud sandbox: gets an idea of the nature of cloud files that might help react quickly to security problems.
Future Of Threat Intelligence
Threat information or cyber threat intelligence is intelligence garnered by combining, analyzing, and interpreting massive data to predict cyber assaults and avoid them.
According to Markets and Markets, threat intelligence could be worth $13 billion by 2023.
The demand for intelligent threat intelligence is rising with intelligent technology becoming incorporated into our everyday lives. As a result, threat intelligence will no longer be a luxury for big corporations. It is estimated that even the smaller organizations will be adapting to them thanks to more and more digital products and services offered and the hyper-digitalization of many, if not all, business processes.














Leave a Reply