Cyber attacks and cybersecurity are the main topics today because the problem of security is very acute. This is because both small and large businesses require protection from cybercrime. Unfortunately, the healthcare industry is no exception and is regularly subjected to various types of cyber attacks. This is where healthcare data security comes into the picture.
According to analysts, over 3 million healthcare records were breached each month from June 2020 to June 2021. In this article, we will look at the main challenges of healthcare cybersecurity, what benefits cybersecurity can bring to this industry, and the main frameworks that stand to protect healthcare. So, without further ado, let’s get started.
Table of Contents
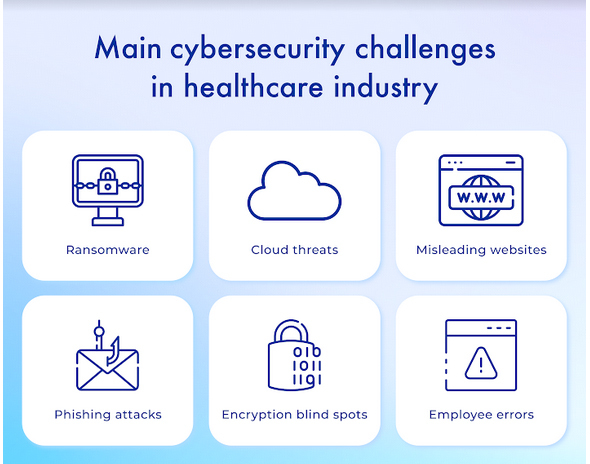
Healthcare Cybersecurity Challenges
Even though cyber threats evolve and become more sophisticated every year, their goals do not change. According to the report, cybercriminals pursue only one goal - theft of personal data that will help in further stealing money. All of this translates into healthcare cybersecurity challenges that the healthcare industry faces every day. Among the most common are:
- Ransomware. Such programs aim to shut down various nodes (servers, other programs, and much more). In return, the attackers ask for a ransom to unblock access to vital business nodes.
- Cloud threats. With the advent of cloud technologies, many industries have started storing critical data in the cloud, and the healthcare industry is no exception. However, if we consider data encryption without proper attention, such an array of data becomes a tidbit for cybercriminals.
- Misleading websites. Such sites are a type of deception and misleading to steal the personal data of ordinary users. Attackers create websites filled with malware and phishing programs and assign them to reputable website URLs. Users should always check HTTPS and a secured padlock before visiting any website. Even, users can click on a padlock to check certificate details. Once you click it, it will show certificate type with brand name like Comodo SSL, Sectigo SSL, etc. A site holder can have many SSL certificate for each domain like single domain SSL, cheap wildcard SSL, multi domain, etc. If there is an SSL certificate, the browser will not show warning, instead it gives insecure connection warning.
- Phishing attacks. The primary strategy of such attacks is to send a considerable number of letters to the database of email addresses, allegedly from a trusted source. All these actions are carried out to entice the personal data of users.
- Encryption blind spots. Encryption is not the ultimate defense against cyber attacks. There is always a chance that a blind spot may be left in your encryption that attackers will exploit.
- Employee errors. With a lack of healthcare cybersecurity awareness among employees, it exposes healthcare facilities to cyber attacks.
Separately, we would like to mention medical devices. In the age of the Internet of Things, when medical devices have access to the Internet, they face the same vulnerabilities as other computer systems. To protect such devices, preventive protection measures must be taken. However, not all medical institutions can carry out these operations in time and become victims of cyberattacks.
Security Breaches Examples
For you to finally make sure that the fantasy of cybercriminals has no boundaries, we decided to give several examples of well-known healthcare cybersecurity breaches of various medical institutions. These real stories show how diverse cyber attacks can be and how you need to be prepared for anything.
1. Lukaskrankenhaus Neuss
Lukaskrankenhaus Neuss is a very famous public hospital located in Neuss, Germany. In February 2016, a cyber attack was carried out on this hospital, which consisted of the following events.
The entire hospital staff faced various error messages related to the ransomware attack. This attack was launched using social engineering tactics (this tactic is the psychological manipulation of people to perform certain actions or disclose confidential information). As a result, the hospital had to urgently shut down all its servers to eliminate it to assess the damage and bring the virus-infected equipment back to normal. While the servers were out, all the medical staff switched to paper documents. In just a few hours of the hospital cyber attack, employees accumulated so many paper documents that it took more than three months to transfer the documents to the database after the cyber attack.
2. Hancock Regional Hospital
Let's move from Europe to the USA. The Hancock Regional Hospital is located in the small state of Indiana and was hit by a massive hospital cyber attack on January 11, 2018. The attack was carried out using the SamSam program and targeted the backup system server. Unfortunately, the cyber attack caused a lot of damage to the hospital since the components of backup files from many systems were corrupted. The only thing left unaffected is the backup files of the electronic medical records.
The goal of the hackers was to obtain a ransom in the amount of 4 bitcoins, which was equal to $55,000 at the time of 2018. Unfortunately, the hospital had no choice but to make a deal with the attackers and pay the ransom.
As you can see, cyber-attacks can wreak havoc on workflows in just a few hours. And all this damage will cost you much more than four bitcoins if you do not take care of the cybersecurity of your medical facility today.
Healthcare Cybersecurity Benefits
If financial and reputational losses have already prompted you to improve your business’s cybersecurity, we want to present you with additional motivation. Breachless cybersecurity of your healthcare facility will bring you additional benefits that it's time to talk about.
1. Lowered Risk of Medical Errors
EHR systems are very popular in medical institutions as they allow you to store all important patient information in a convenient place and have quick access to it. However, a considerable amount of data is a target for cybercriminals. If the healthcare data security is compromised or access is denied, this will affect the hospital's workflow and may lead to casualties. A well-crafted EHR cybersecurity scheme will protect and prevent such attacks.
2. Enhanced Patient Privacy
Healthcare data security always comes first. Poor protection of patient data can lead to their theft during a cyber attack (attackers can steal bank account data, insurance data, and much more). In addition, such negligence can lead to legal problems for the hospital.
Take care of reliable cybersecurity of your patients' personal data to avoid theft and further proceedings with legislative bodies that will entail reputational losses for your medical institution.
3. Safer Technology Adoption
The increased risk of falling prey to cybercriminals affects the speed of progress. Because of this, many hospitals are afraid of increased vulnerability and are in no hurry to introduce new technologies into their work processes. And they can be understood.
However, any development entails the introduction of new tools. If a medical institution wants to provide top-class patient care, it must step out of fear and introduce new technologies. However, it is worth conducting a global audit of the available technologies and consulting about cybersecurity specialists before doing this. They will think through the ideal implementation process and provide preventive measures against healthcare cyber attacks.
4. Better Patient Care
In the examples of cyber attacks that we gave earlier, you can notice that attacks were carried out on important nodes. For troubleshooting, you had to turn off the servers and switch to traditional methods of keeping records. And such an abrupt transition can not only slow down service and care for patients but also lead to a total failure of the health care system of a particular medical institution. With meticulously crafted cybersecurity, you protect yourself from the possibility of stalling customer service. In addition, hospital staff will work more efficiently, knowing that all work processes are protected against cyber attacks.
5. Safer Operation of Medical Devices
Connected devices are also gaining popularity in the healthcare industry. However, such devices are also susceptible to healthcare cyber attacks. For example, in January 2020, 6 critical vulnerabilities were found in GE healthcare devices. Attackers can take advantage of these loopholes and change the functionality of a device or completely disable it. If this happens to some kind of life support device or X-ray machine, it endangers the lives of your patients. That is why it is crucial to implement the latest healthcare IT security techniques.
Why Frameworks Are The Main Healthcare Cybersecurity Tools
When it comes to cybersecurity in healthcare, it’s all about frameworks. But why are frameworks such an effective defense against cyber attacks? There are two reasons for this:
- Reason 1. Cybersecurity frameworks are designed primarily to identify, detect, respond, protect and recover from the impact of healthcare IT security threats and their consequences. All frameworks are a compilation of healthcare information security practices that are designed to protect businesses from intruders.
- Reason 2. Let's take one of the most popular NIST frameworks as an example. This framework is built to provide security using its core elements, implementation levels, and a profile that aligns them with business requirements, financial capabilities, and risk tolerance.
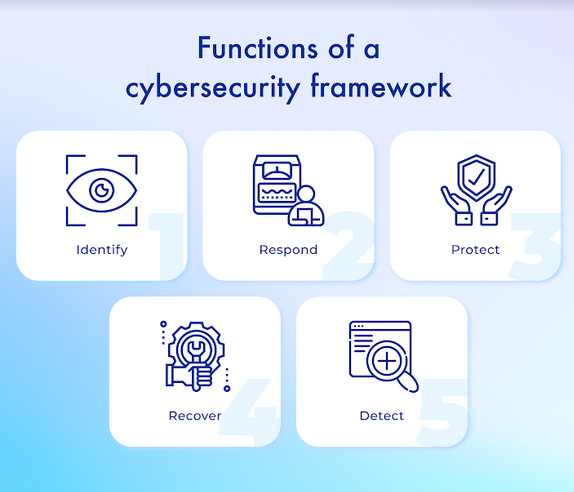
The result of these reasons is improved management of the security of a medical institution and, accordingly, greater protection against various cyber attacks.
Healthcare Cybersecurity Frameworks You Should Be Aware Of
Now is the time to talk about the main tools for healthcare cybersecurity, namely frameworks. We have collected the five most popular frameworks and will tell you more about each in more detail.

Framework 1. NIST
We have already mentioned this framework today in the article, and it is time to get to know it a little closer. NIST CFS is at the top of the line among all frameworks in many industries, including healthcare. However, the main trump card of this framework is support for a large number of documents, and the most famous are the following:
- NIST Framework for Improving Critical Infrastructure Cybersecurity
- NIST SP 800-53: Security and Privacy Controls for Federal Information Systems and Organizations
- NIST SP 800-171: Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations
NIST CFS was developed based on modeling of various cyber threats, their analytics, and collaboration. This framework helps improve cybersecurity in healthcare facilities and their internal processes to unprecedented heights, making healthcare secure.
Framework 2. HITRUST
HITRUST stands for the Health Information Trust Alliance. As you can see, 26.4% of users in the healthcare industry adhere to this framework when setting a high level of cybersecurity in healthcare facilities. HITRUST is a private organization whose founders are top-class specialists in the medical industry. The HITRUST program includes general risk identification, assessment and assurance methodology, cybersecurity training, and awareness of medical staff. In addition, it is fully compliant with ISO / IEC 27001: 2005 security protocols. This way, it ensures healthcare IT security.
Framework 3. Critical Security Controls
Critical Security Controls is developed by the not-for-profit organization Center for Internet Security. At its core, this framework is an extensive list of various methods that aim to prevent and stop the most common cybersecurity threats in the healthcare industry. In CSC, all controls are arranged in descending order, from most important to least important. These include managing various vulnerabilities, creating an asset registry, and more.
The noteworthy fact is that Critical Security Controls is not used as an independent framework since it is not a separate solution. However, it can often be seen in conjunction with more famous frameworks like NIST and others.
Framework 4. ISO 27000 Series
ISO is the International Organization for Standardization that every software developer knows because it is responsible for the security of personal data and not only. This organization develops various healthcare information security standards and protocols for the industries. If you decide to start healthcare mobile app development for your business, you have to make sure that you are ISO compliant. The most famous protocol is ISO/IEC 27000, which aims to maintain security and information security.
Framework 5. COBIT CFS
COBIT Framework is an acronym for Control Objectives for Information and Related Technologies. This framework is an IT management tool. However, this does not mean that it is not applicable in the healthcare sector. Many companies use COBIT CSF to implement various practices mandated by other security standards, such as the NIST Health Cybersecurity Framework and ISO 27001/2, and many others.
Wrapping Up
As you can see, cybersecurity in healthcare is an issue that needs special attention. If you carelessly approach it while opening your medical facility, you risk becoming a victim of a cyber attack that will entail financial and reputational losses. In addition, you risk the health and lives of your patients. Therefore, it is very important to be as responsible as possible when working with cybersecurity in the healthcare sector. Frameworks are designed to help you make your business more secure and take preventive measures against cyber intruders.













Leave a Reply